How to secure your EC2 instances replacing SSH
With a simple Google search we can find a few million results with the terms of “EC2 SSH”, and whit these, ways to enable SSH in our instances. In the other hand, only a few thousand appears with “EC2 SSM”.
Why is that if the title of this post is talking about securing the EC2 instances replacing SSH, is SSH not secure?
The problem is not that SSH isn’t secure enough, is that you want to reduce the attack surface as much as possible.
The attack surface of a software environment is the sum of the different points (the “attack vectors”) where an unauthorised user (the “attacker”) can try to enter data to or extract data from an environment.
Reducing the attack surface can be done in multiple ways, i.e. running your code in a private subnet when possible, IP whitelisting to limit the access to your cloud environment and so on.
Ditch SSH using AWS Systems Manager (the right way) and secure your EC2 instances
SSM is a great service which allows you to do multiple things, one of those is to replace SSH.
To be able to use SSM you need to follow three simple steps:
- Install SSM agent in your EC2 instances. It comes pre-installed in a few AMIs, so you might be lucky.
- Once you have SSM agent installed, you need to grant access to your EC2 instance to talk to the SSM API, for this you need to attach a role to your instance. Create a role and assign the ‘AmazonSSMManagedInstanceCore’ policy.
- Finally, the user will need access to use SSM, this can be enabled attaching a policy like ‘AmazonSSMFullAccess’.
Let's start using the SSM
Log in into the AWS console, navigate to the AWS Systems Manager service dashboard, open the Session Manager, select your instance and click ‘Start session’ you should be able to see something similar to this:
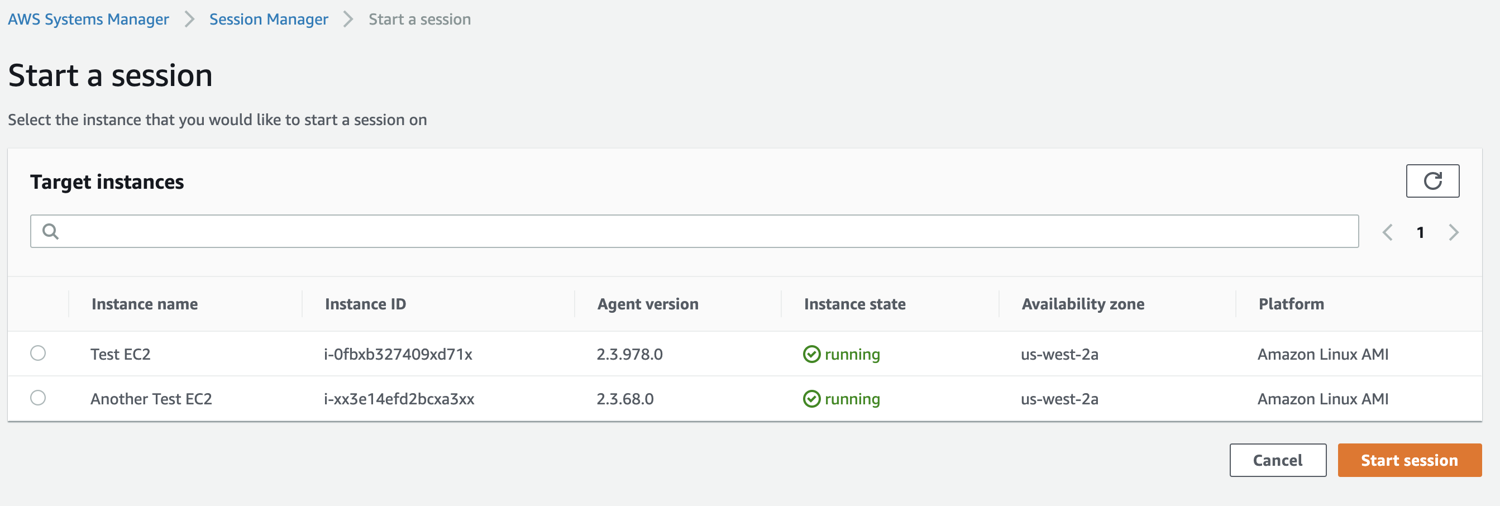
After starting a session you can start using it as if you were in your terminal
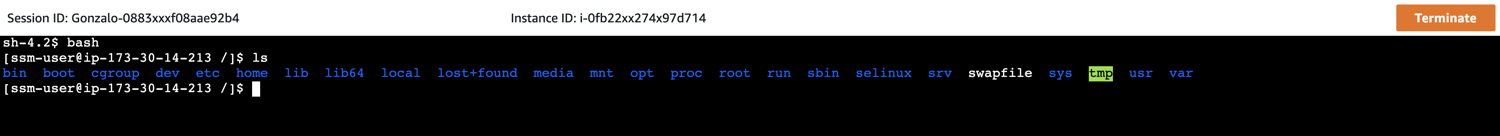
This comes handy to use from time to time, but as a daily tool, is not practical at all. You don’t want to do all this every time you need to run a command in your EC2 instance, and also you might want to have several sessions at the same time, which is not possible using the console.
Use AWS CLI to start an SSM Session
If you want to use the AWS CLI to start and end sessions that connect you to your managed instances, you must first install the Session Manager plugin on your local machine.
Now you can start a session using SSM, and use it as good old SSH.
aws ssm start-session --target <instance-id> --region <region> --document-name AWS-StartInteractiveCommand --parameters command="bash -l"
I was having the “An error occurred (TargetNotConnected) when calling the StartSession operation:” Error because I did not specify a region in the connect command, this might not be an issue for you if you only use one region.
Using SSH through SSM
Ok, you might think I’m crazy reading this, at this point, why would we use SSH?
The idea is that we can use SSH through SSM, there is no direct connection between your machine and the instance, everything runs through AWS Systems Manager service, which means you can still have your port 22 closed in the EC2 instance.
This also gives you the ease of using SCP as you would normally do to copy or download files.
# Use it as you would with SSH, but the host is the Instance ID
# ssh -i ~/.ssh/my-key-pair.pem i-0fb12332740912314
#
# If you want to specify the user:
# ssh -i ~/.ssh/my-key-pair.pem another-user@i-0fb12332740912314
#
# If you want to use a named host:
# ssh my-host-name
# Default user
Host *
User ec2-user
# SSH over Session Manager
Host my-host-name
Hostname i-0fb1255540912314
IdentityFile ~/.ssh/my-key-pair.pem
ProxyCommand sh -c "aws ssm start-session --target %h --document-name AWS-StartSSHSession --parameters 'portNumber=%p'"
Host i-* mi-*
ProxyCommand sh -c "aws ssm start-session --target %h --document-name AWS-StartSSHSession --parameters 'portNumber=%p'"
You can even take it further and use some tools like ssh-over-ssm if you like.
Summary
- Replacing SSH with SSM, it’s quite easy and straight forward.
- You can create more granular access if needed by creating multiple policies with different access levels for each one, allowing some engineers to access only a subset of your EC2.
- Enabling SSM removes the need to expose the port 22 in our EC2 instances, which as we mentioned before reduces the attack surface of our AWS account.
- Using SSM instead of SSH removes the problems of having to rotate pair keys every so often.
- You can still use it as SSH / SCP as always